Overview
After requesting a proof, the next step is to use that proof in the application’s workflow. The exact way proofs are used will vary depending on the architecture of the application. However, there is a common pattern; once a proof is received from the Boundless market, the next step will be to verify that proof onchain.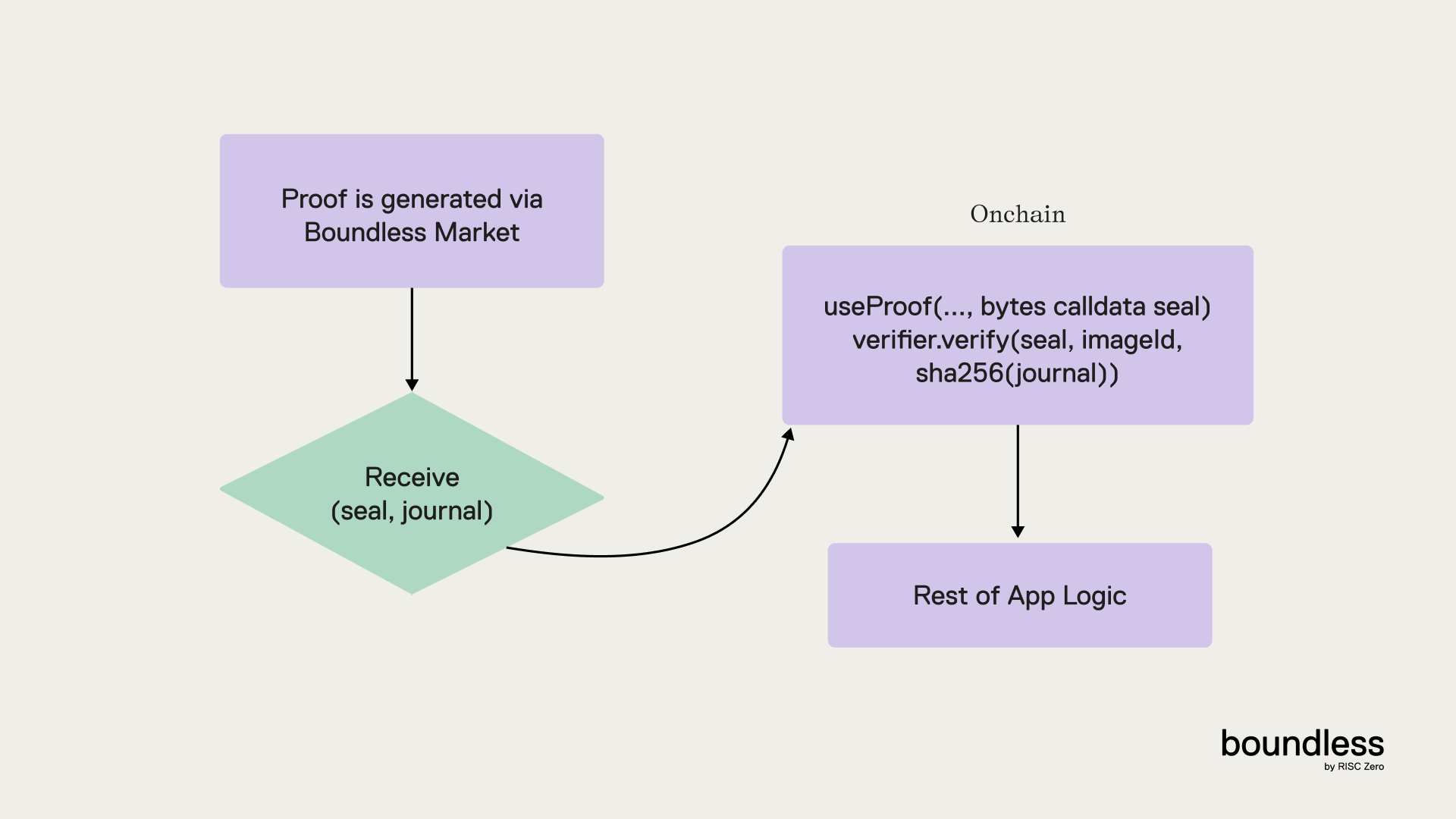
Proof Verification
The Boundless Foundry Template, walks through a simple application which, with an input number, x:- Uses a simple guest program to check if x is even.
- Requests, and receives, a proof of x being even from the Boundless Market.
- Calls the
setfunction on theEvenNumbersmart contract with the arguments: x and the seal (the proof bytes). - The
setfunction verifies the proof that x is even; if the proof is valid, thenumbervariable (in smart contract state) is set to equal x.
EvenNumber.sol contract.
To create an EvenNumber contract instance:
set function on the EvenNumber contract, a “set number” transaction is created:
set function on EvenNumber.sol:
[EvenNumber.sol]
set function will verify the proof via the RISC Zero verifier contract.
The verify call will revert if the proof is invalid, otherwise the number variable will be updated to x, which is now certainly even.
Each application will have its own requirements and flows, but this is a common pattern and a good starting point for building your own application.
Relevant links: Boundless Foundry Template, Journal, Seal